Earlier this year, we opened up Sidekick for early access as we continued to refine its features in preparation for today’s launch. Now that we are here, we would like to officially introduce you to Sidekick - your AI-powered extension to Binary Ninja that makes reversing easy.
Take a look below at the ways Sidekick applies AI to help solve your reversing problems:
Over the next few weeks, we’ll be posting more blog entries highlighting both the features of Sidekick in greater depth and also some of our motivations for developing and releasing an AI-based product and service, so stay tuned!
Read on for all the details but if you’re ready to just try it now, head over to the Sidekick website and sign up today.
Improved Decompilation
Sidekick builds on Binary Ninja’s existing performance and capabilities for disassembling and decompiling binaries in order to improve the clarity of the code for faster, deeper understanding.
Structure Recovery
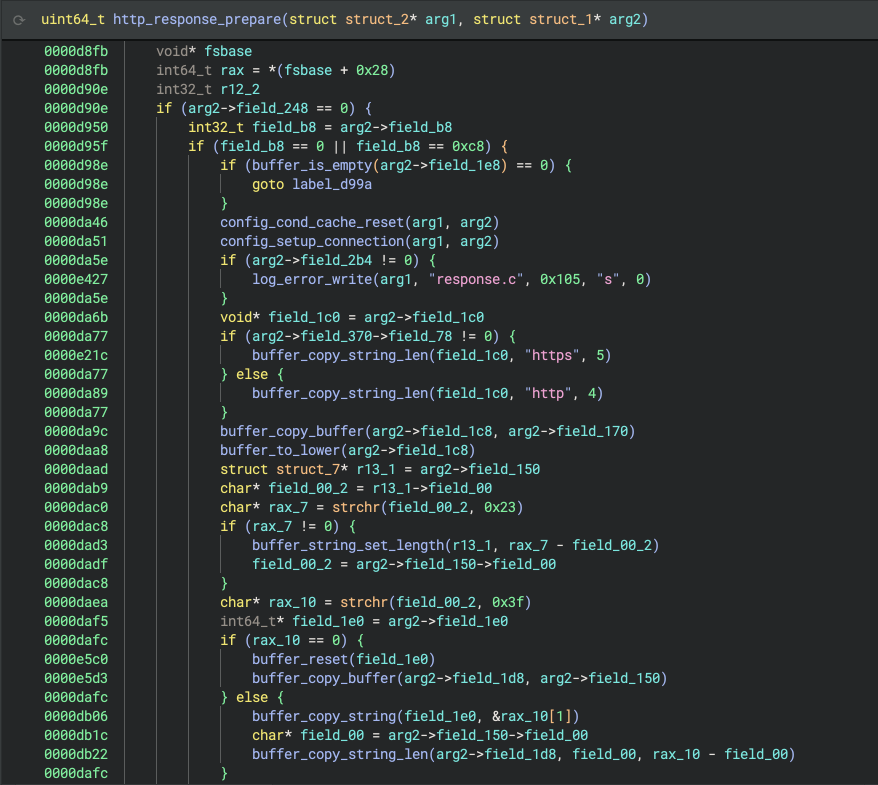
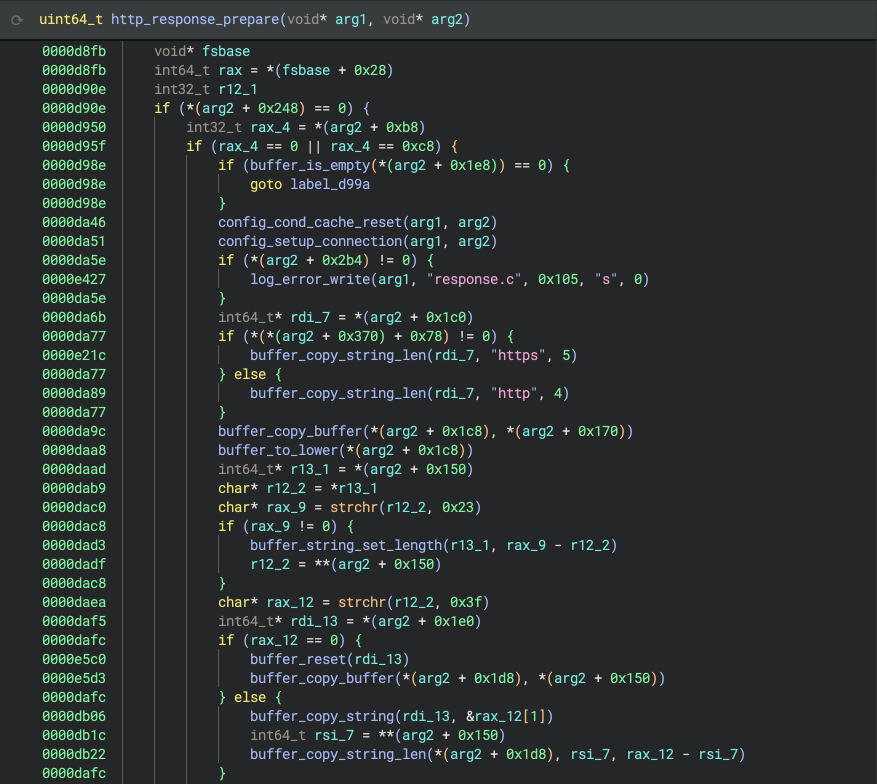
Structures are often used to manage information used by the program. At the binary level, the various fields that comprise structure definitions are accessed via pointers and offsets. Traditionally, reverse engineers spend hours manually deciphering structure layouts by meticulously tracing memory accesses and analyzing field data types and sizes.
Sidekick automates this intricate and tedious process by intelligently analyzing the code, identifying and defining referenced structures, and presenting them cleanly within the Binary Ninja Types Sidebar, saving you valuable time and effort.
Suggestions
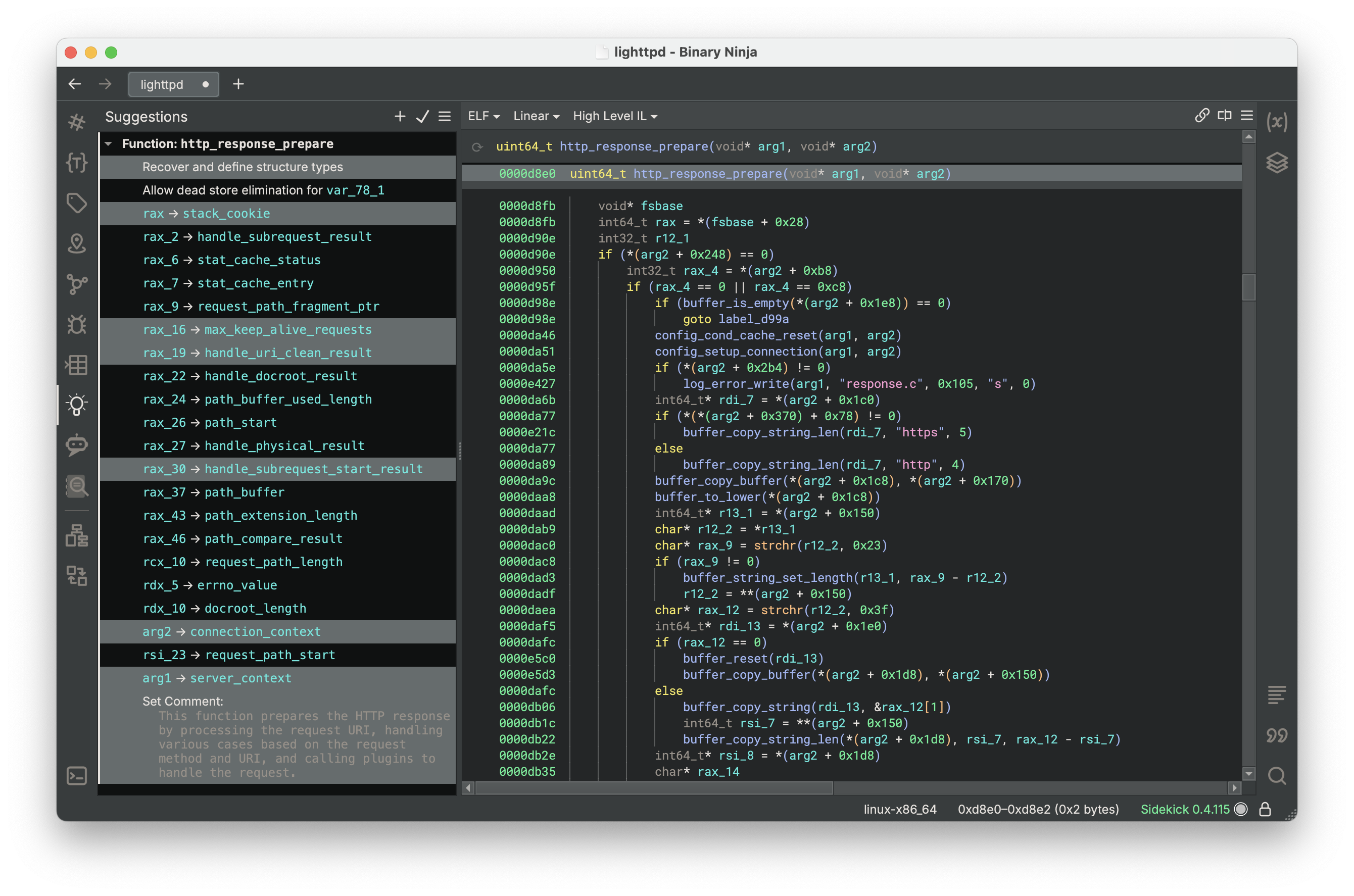
Sidekick analyzes the binary and presents a range of suggestions that you can automatically apply to improve decompilation, including recovering structure types, naming structures and fields, naming variables, naming functions, summarizing functions with function comments, and more.
To help show the value of this feature, take, for example, the task of reversing a function with no variable names, symbols, or documentation. Traditionally, this process can involve examining each line of code, interpreting its instructions, tracking the definitions and uses of variables in the context of their associated operations, and manually assigning meaningful names to them. This not only takes valuable time and effort but also demands a high level of knowledge and skill in reverse engineering. This becomes even more intensive as the size, number, and complexity of functions increase for binaries.
Now, within seconds, Sidekick gives you access to clear, concise names for variables, arguments, structures, and functions and informative function summaries, enabling you to quickly grasp what the code is doing.
Inline Comments
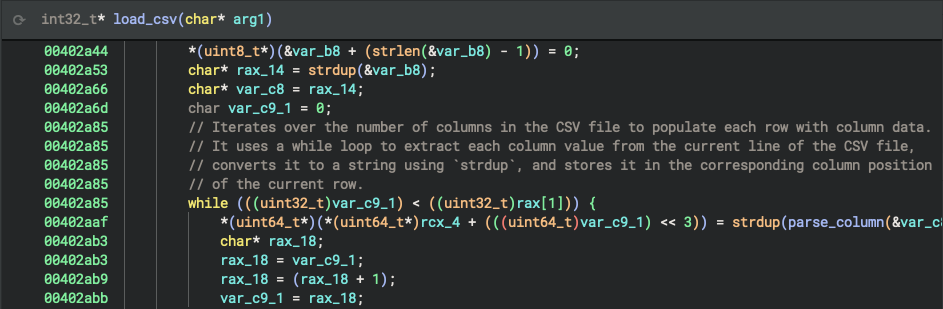
Sidekick also enables you to automatically generate and apply inline comments that explain and summarize the lines of code you select. This feature comes in handy when you come across uncommon instructions or complex logic whose purpose is not immediately apparent, which takes time and effort to research, analyze, and understand. With the quick click of a button (or press of a key), Sidekick breaks through the convolution with a clear, concise description of the code.
Deeper Analysis
At some point, you may want to go beyond just making the code more readable and need to start analyzing the code to either understand it better or discover its properties. Sidekick can help with that.
The Assistant
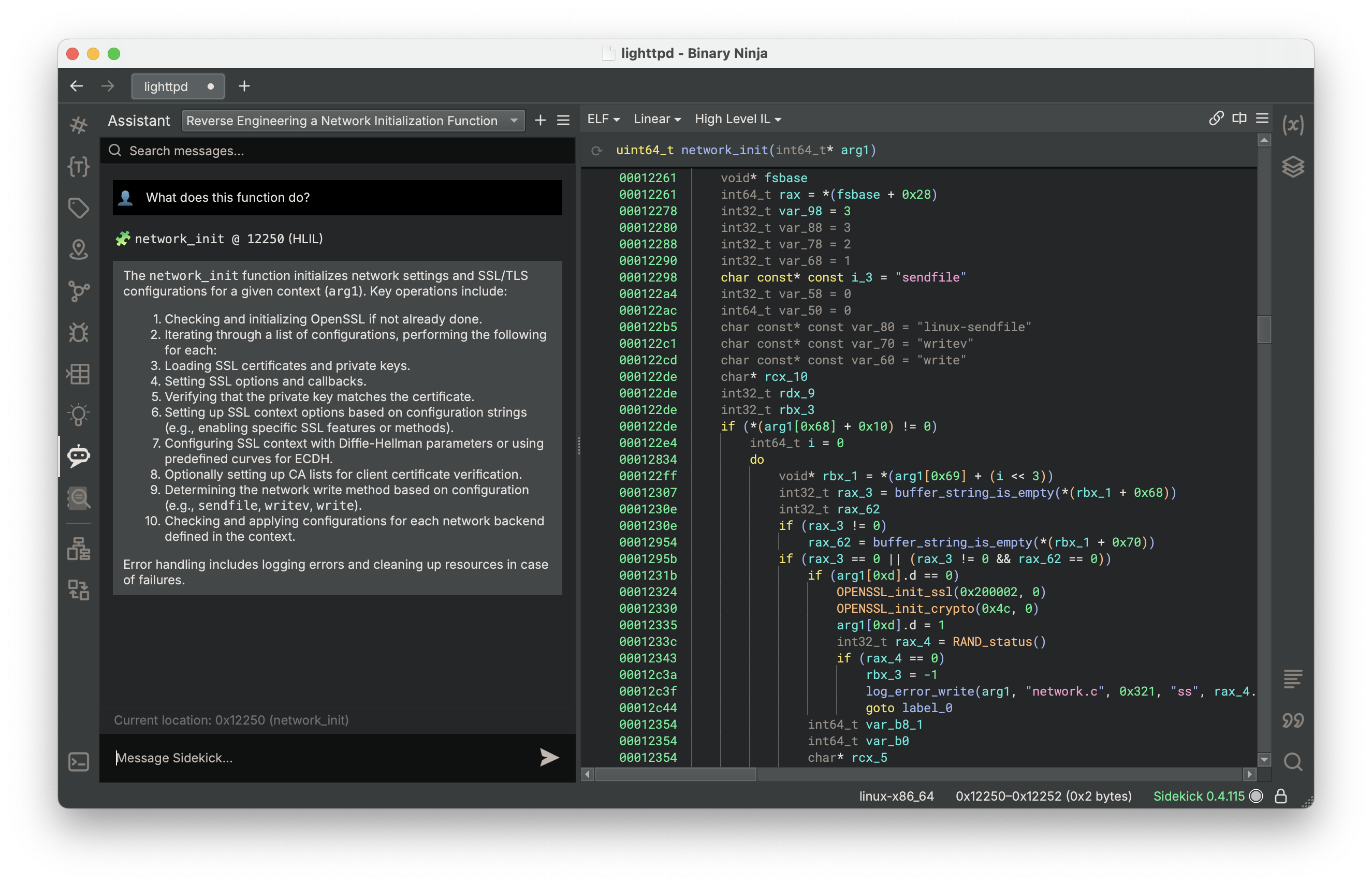
Sidekick enables you to drive a discussion and analysis of your binary with an AI assistant that possesses a vast amount of knowledge and code reasoning capabilities useful for reversing.
- Are you curious about what the current function does? Ask the Assistant.
- Are you not sure what some of those exotic assembly instructions do? Ask the Assistant.
- Are you looking at a Windows binary, but don’t know much about the Windows APIs? Ask the Assistant.
- Do you need a rough implementation of the current function in Python? Ask the Assistant.
Investigations
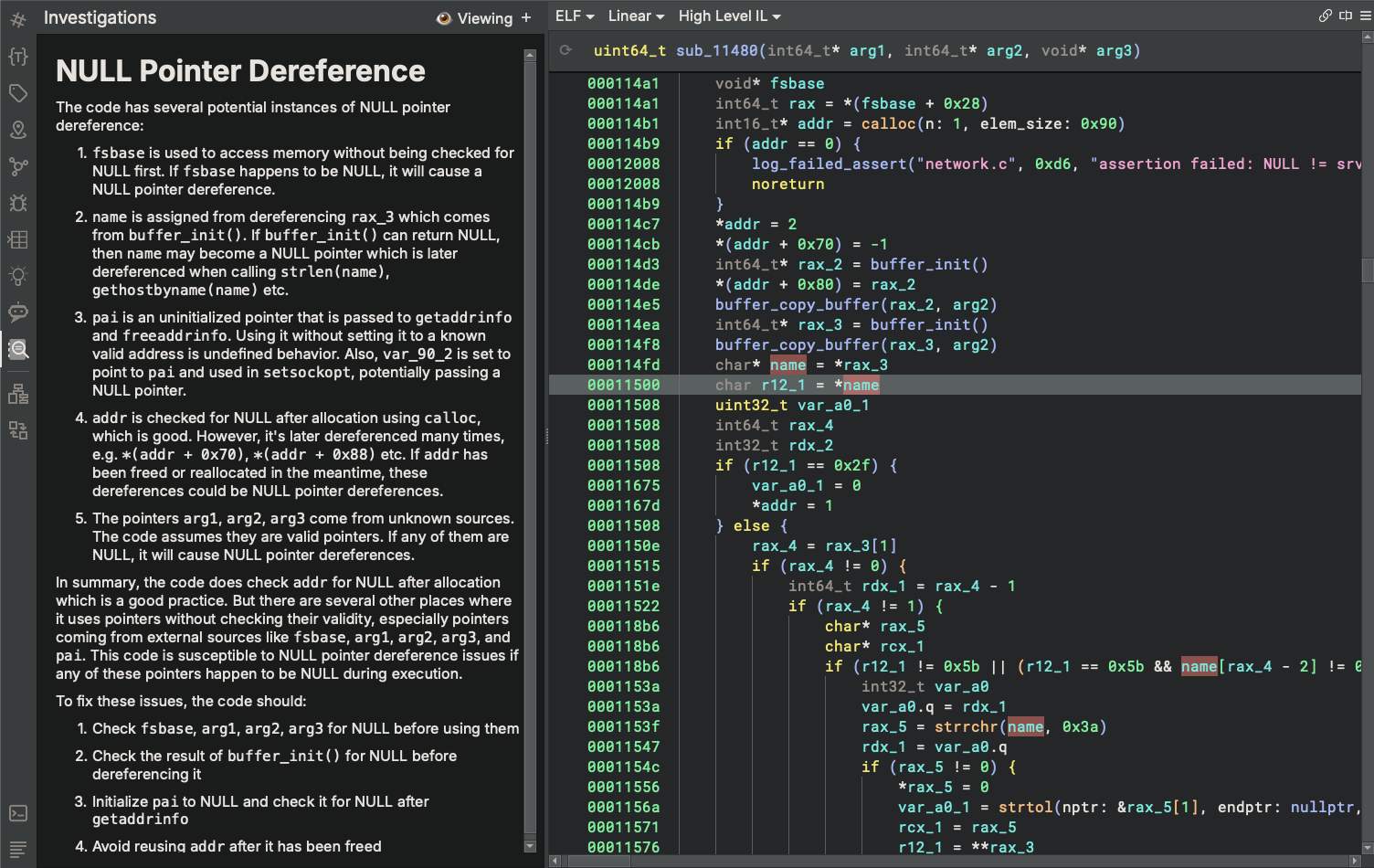
Sidekick also gives you the ability to launch safety-focused investigations of the binary, where Sidekick drives the analysis, looking for evidences of vulnerabilities you’re interested in exploring. Maybe you suspect the code you’ve been staring at for a while now has a specific bug in it, but you’re just not sure. Or, maybe you’re generally looking for any vulnerability any where. Let Sidekick to do the work for you while you concentrate your time and skills on tasks aligned with your expertise.
In future releases, we are planning to extend this feature to support more vulnerability classes, to perform multi-step analyses, and to prompt the user for input when Sidekick needs more information or guidance to continue investigation. So stay tuned!
Sophisticated Search
When opening a binary for the first time, you typically try to find the functions that are worth focusing your reversing efforts on. Sidekick includes features specifically designed to help you do this.
Indexes
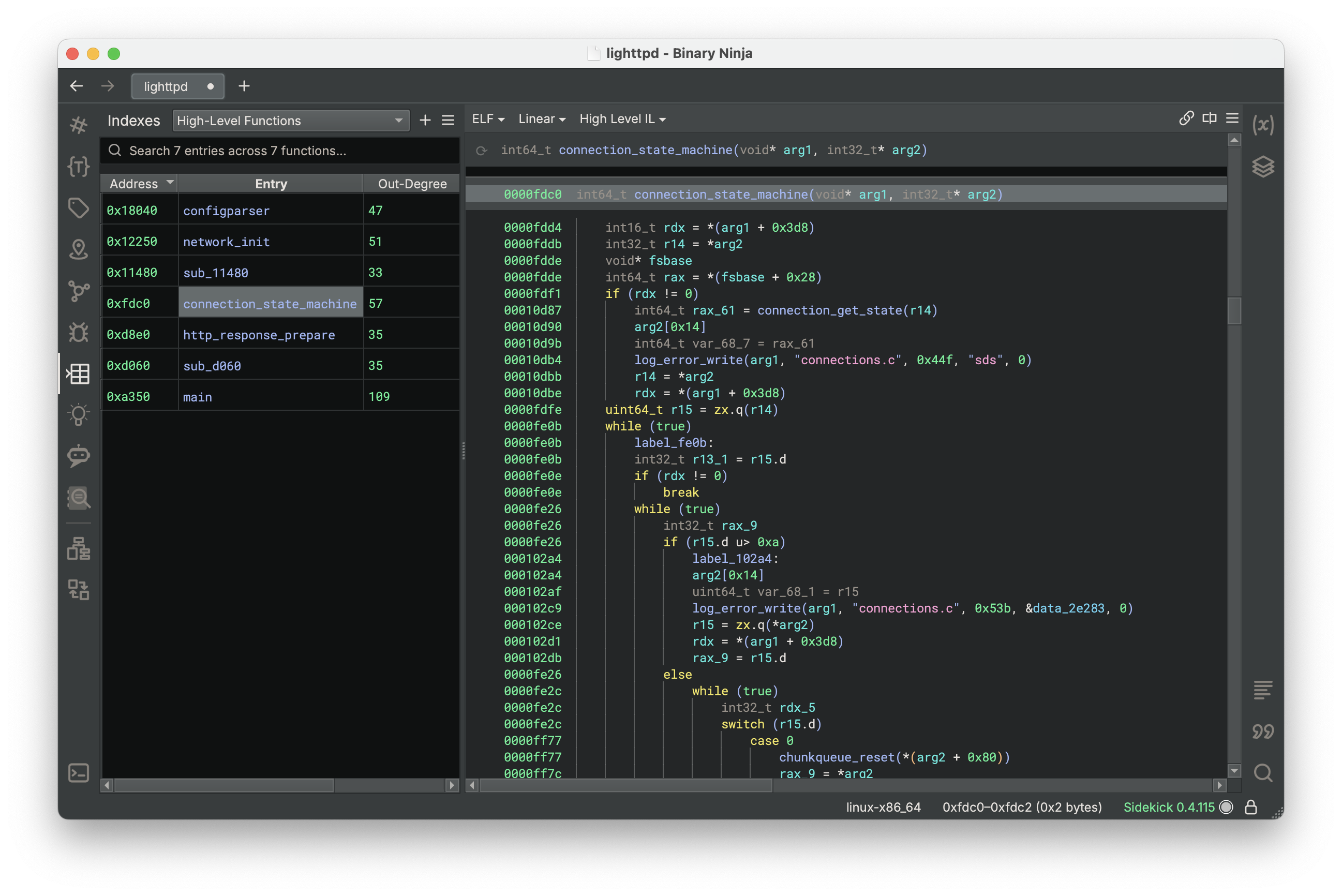
Indexes is a feature within Sidekick that enables you to quickly find items in the binary that you’re looking for, similar to how an index in the back of a book contains topics and the locations in the book where they’re found. Indexes automate the search process by executing scripts that use the Binary Ninja API to identify, locate and return items of interest. These items are displayed in a simple table with built-in navigation.
Let’s say you wanted to find all of the instructions in the binary that call a network-related function. To do this manually, you might try the following:
- Open the list of symbols in the binary
- Scan through the names of symbols looking for something related to networking
- Navigate to each of those functions and view their call-sites
- Take note of them by adding a tag or comment so that you can search for or view them later
This process takes time to look at each symbol, knowledge and/or skill to recognize network-related functions, time to navigate to and view call-sites of the function, and time and effort to make note of each call-site. You could improve this process by writing code using the Binary Ninja API to automate scanning for network-related symbols using a variety of methods (e.g. hard-coded list, ML-based classifier, etc.). This also takes time, effort, knowledge and skill to implement.
Sidekick cuts through all of that with a few, simple button clicks and presents a table of network calls that you can click and navigate to.
To make this feature more useful out of the gate, we have provided a catalog of pre-defined indexer scripts for commonly searched items.
Need something more than what’s in the catalog? You can request Sidekick to automatically generate an indexer script from your own natural language description of what you’re looking for. Alternatively, you can still take the time to manually write your own indexer script if you want.
Code Insight Map
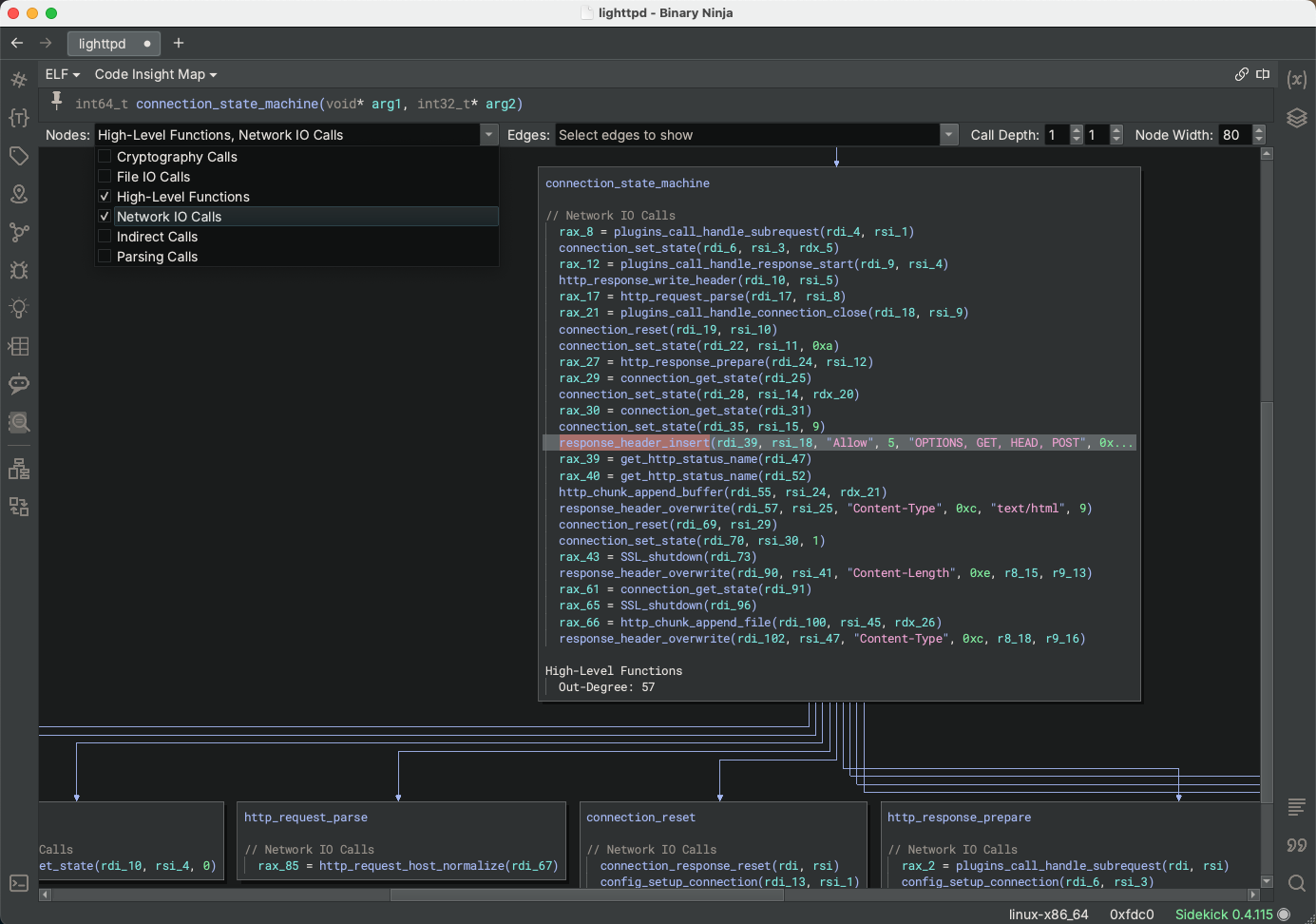
The Code Insight Map is another feature within Sidekick that helps you quickly obtain a top-level understanding of the structure and functionality in the binary. The Code Insight Map is a graph-based interface that allows you to explore the content of and relationships among a focused set of topics. It relies both on items generated from the Sidekick Indexes and the calling relationships between functions in the binary in order to display this focused view of the code.
Think of it as a hybrid between a dynamic slice and a call graph, except you control the items of interest and it can include far more context than what a single slice would.
Existing graph-based tools often display too much information that overwhelms the user and prevents understanding. The Code Insight Map reduces the time and cognitive effort to develop an overall picture of the binary by enabling you to filter out irrelevant information and select only the items you are interested in seeing.
Summary
Sidekick makes reverse engineering easy. Check out the free plugin in the plugin manager, or sign up for a paid account to enable all of the advanced AI functionality.