What does it take to almost completely re-write a full architecture module to get the highest accuracy AArch64/ARMv8 decompilation and lifting? Follow along as we not only talk about the improvements we’ve made since open sourcing it in October 2020, but also take a behind the scenes look at the new disassembler and how it was generated it from the ARM specification.
Read more...Binary Ninja Blog
As we settle into our quarterly release cycle, this stable update includes changes from the past four months of Binary Ninja development. With over 600 commits and 157 issues resolved across an increasing number of repositories (most of which are open source), we continue to simultaneously launch new features, improve existing features, and resolve bugs.
The main new features for this release include new view-synchronization, type and variable cross-references, and a plethora of HLIL improvements. Read on for more!
Read more...Today’s entry is a guest-post brought to you from our friends at Kryptos Logic who have been working on a handy plugin we wanted to highlight. They were kind enough to let us cross-post their blog here, but make sure to check out the rest of their posts as well! Note, everything below this paragraph is from Jamie Hankins, not Jordan despite what the “author” tag on this post says!
Read more...It’s only been five months since the release of our HLIL decompiler and we’ve been busy on lots of fronts! Note only are we in the middle of open sourcing all of our core architectures, but we’re also launching a welcome back discount for customers who have had their support expire and are thinking of coming back and seeing everything that’s changed.
And speaking of what’s changed, just in the past three months since our last release we’ve almost 800 commits across our different repositories! That’s a lot of new changes to cover, so this is definitely not an exhaustive list, but let’s dig in!
Read more...Vector 35 has a history of releasing lots of open source. We not only released the entire Binary Ninja API under the MIT license, but all API docs, and user docs as well. We continue to release high quality official plugins under open source licenses and even released the entire python prototype of Binary Ninja!
That said, we’ve long planned on doing even more and I’m pleased to announce that today we’re publishing the first of several of our internal core architectures: ARMv7/thumb2 and Arm64 (aarch64) under an Apache 2.0 license! These join our already open source PPC architecture, and will be followed up by our remaining core architectures: x86, x64, and MIPS architectures over the next few weeks.
Read more...[Editor’s Note: This blog entry is brought to you by another of our summer interns, Chinmay. You can find more about him at his personal site. Also, be aware that this feature is currently only available on the development branch of Binary Ninja and some users may need to switch branches if they are not already on dev.]
Binary Ninja now implements User-Informed DataFlow (UIDF) to improve the static reverse engineering experience of our users. This feature allows users to set the value of a variable at the Medium-level IL layer and have the internal dataflow engine propagate it through the control-flow graph of the function. Besides constant values, Binary Ninja supports various PossibleValueSet states as containers to help inform complex variable values.
[Editor’s Note: This blog entry is being brought to you by one of our summer-interns, Xusheng. You can find more of his writeups over on his github page.]
The last week’s challenge was created by Dennis Yurichev. It is also hosted on crackmes.one. The challenge is compiled by a modified Tiny C Compiler (TCC) which obfuscates the generated code during compilation. We will cover the major techniques to deobfuscate the binary, followed by a quick analysis of the algorithm itself.
Read more...While many of our users are already happily using it on the dev channel, we’re pleased to announce the release date for our decompiler/HLIL on the stable channel is May 20th, 2020.
That’s right, the long awaited Binary Ninja 2.0 is arriving in only 10 days.
With the 2.0 release comes several important changes. First, we’re including the decompiler for all current customers at no cost. All users, both commercial and non-commercial with active support will be able to download the stable update (and indeed they can all try it now just by switching to the dev channel). Second, we’re raising the base price of all versions. This reflects the increased value provided by the decompiler as well as helps us build new features at an even faster rate. See below the fold for more details.
Read more...It’s been over a month since we announced the Binary Ninja Debugger Plugin (BNDP) in beta, and as it begins to near the time it can shed its “BETA” tag, we wanted to show off the current state of the features and capabilities. Note that the debugger is being implemented as an open source plugin and feedback and code are always welcome.
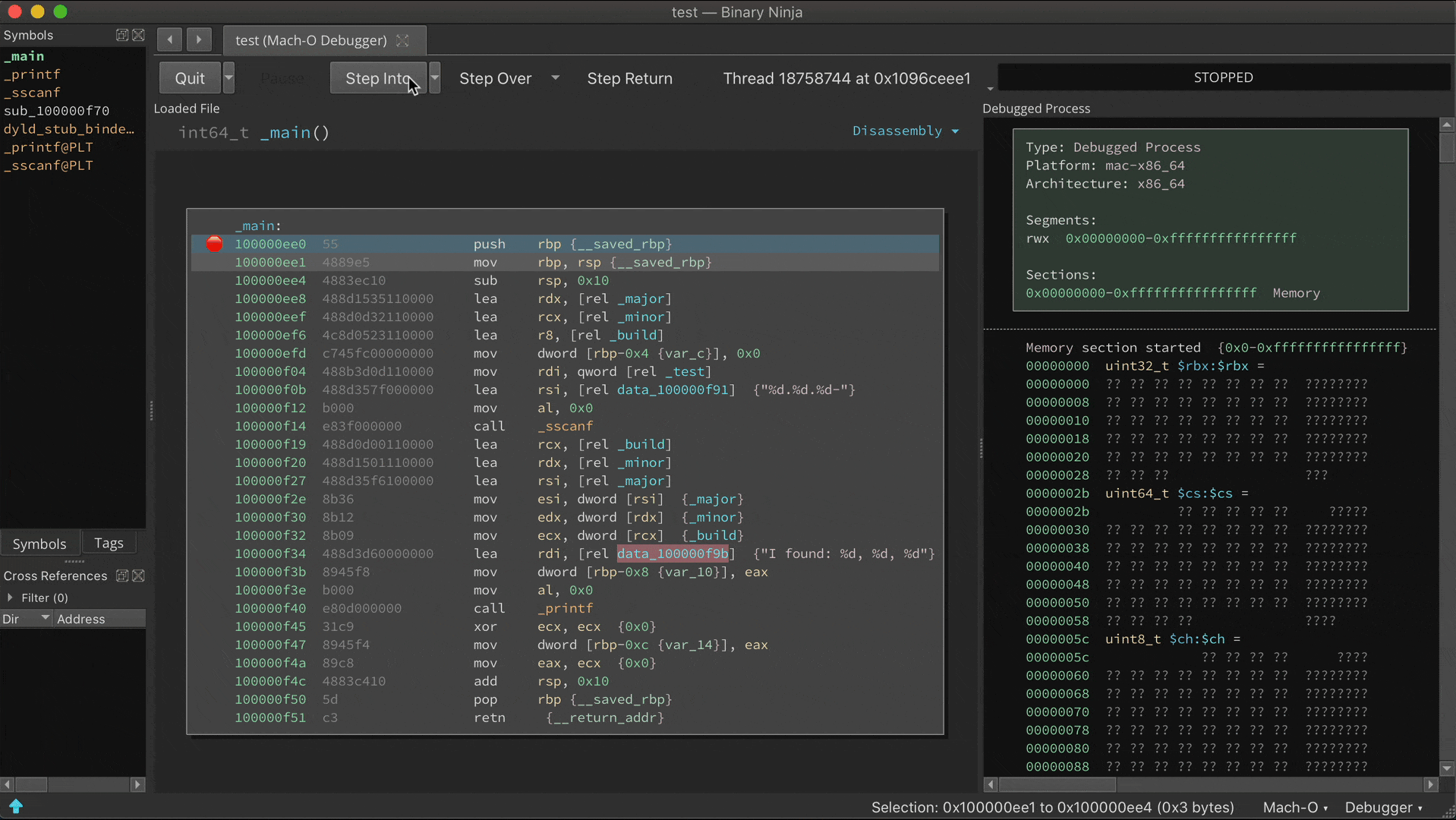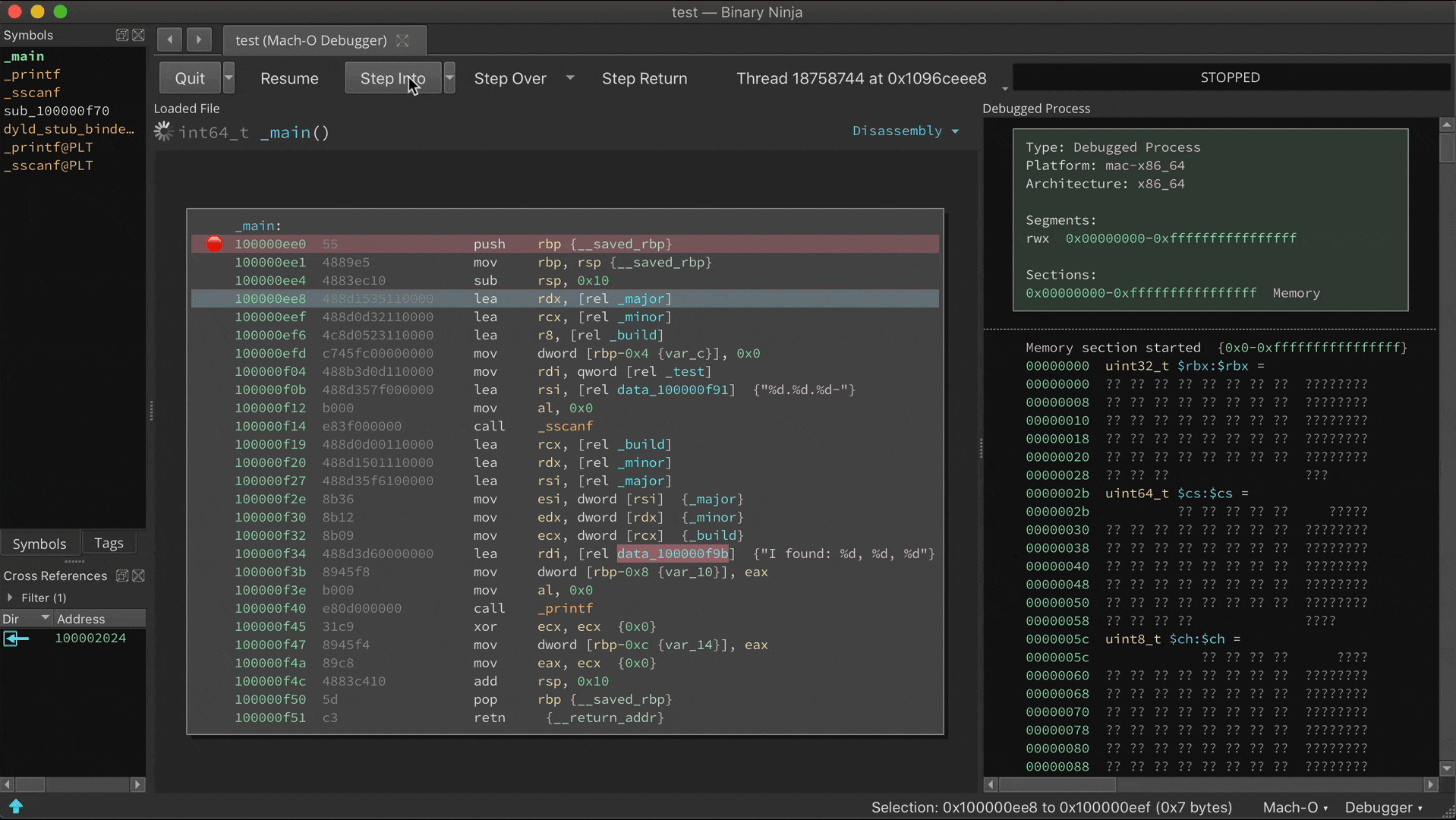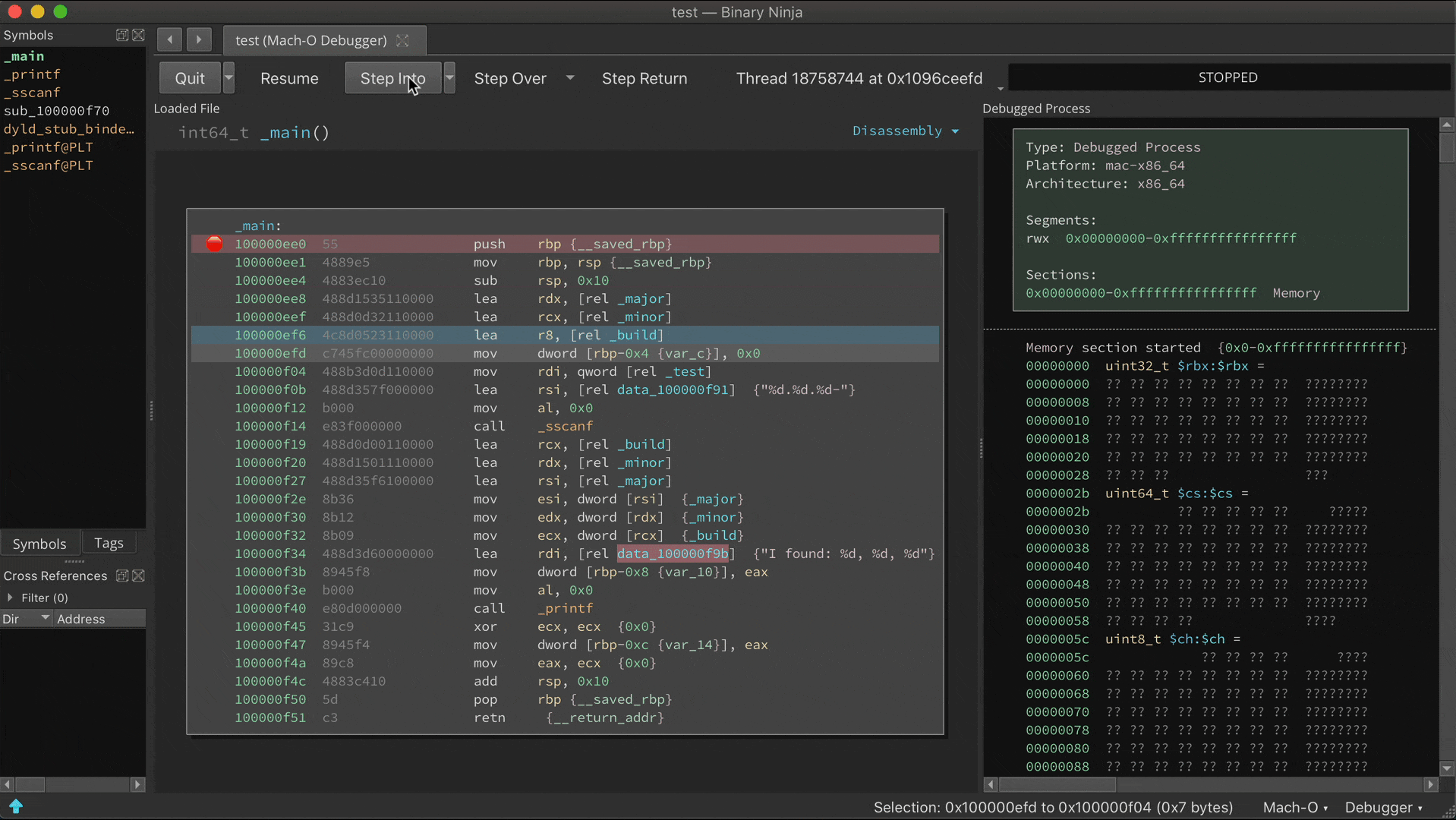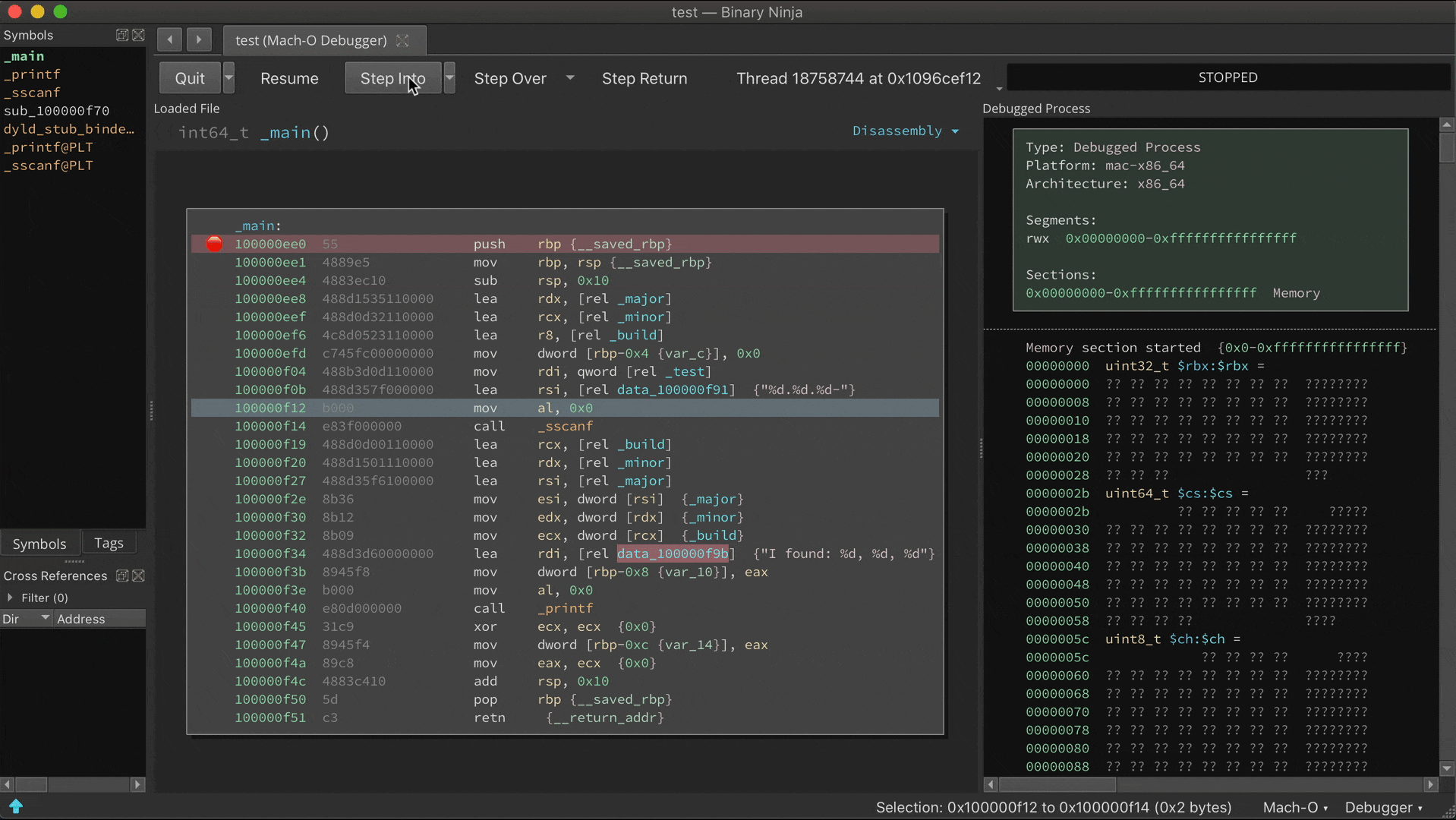
Whew, what a crazy time it’s been lately. The world is in lock-down due to coronavirus but thankfully V35 has been able to keep working safely with everyone at home. Well, as long as you consider work-from-home with kids “safe” for some of us. We miss the office conversations and collaboration, and we’ve had to make do with fragging each other in online games and occasional video chats.
In the meantime, we’ve been able to make a ton of progress in the last several months and we’re nearing the release of our first 2.0 dev release which includes our decompiler and HLIL!
Because we’re going to have a lot of blog posts and updates coming out over the next few weeks, we wanted to make sure we got a State of the Ninja out of the way beforehand to get everyone up to date on what has happened lately.
Read more...« Previous Page: 9 of 12 Next »